Office 365 has a dominant share of the cloud email market. As such it is a very tempting target for cyber criminals to try and exploit. With just one well-crafted email they can gain access to your entire Office 365 account and possibly other corporate systems and data. This could result in not only severe financial loss but your reputation could also be irrevocably damaged.
Current anti-malware services are pretty good at catching the majority of most mass spam attacks but cyber criminals are always innovating and finding holes in these systems.
PhishPoint is the latest threat that manages to completely circumvent all of the normal defenses and as such often goes completely undetected. Anti-malware services usually compare links inside an email with known malicious sites or if the links are trying to camouflage their true destination and deals with them accordingly.
However, what if the link is completely safe within that email but still leads the user to commit a harmful action? How would an anti-malware service know if the link does not point to anything malicious?
This is how PhishPoint works. Hackers setup free trials of Office 365 then upload SharePoint documents to Office 365 to house the real phishing links. You then receive an email inviting you to access and edit the SharePoint document. This is a legitimate SharePoint request, so it will make it through the malware-scanning service and straight into your inbox.
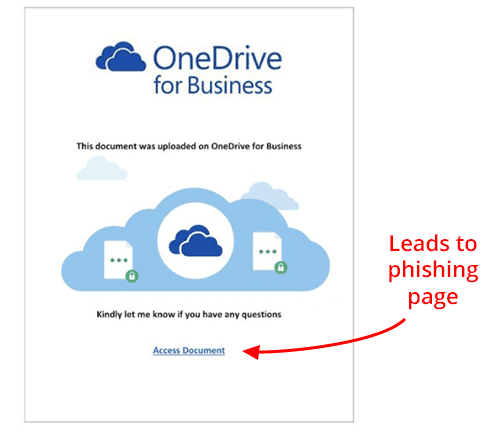
The file shared is made to look like a OneDrive file, when the user attempts to open the file they are presented with content that impersonates a standard SharePoint request to access a OneDrive file that displays an “Access Document” link.
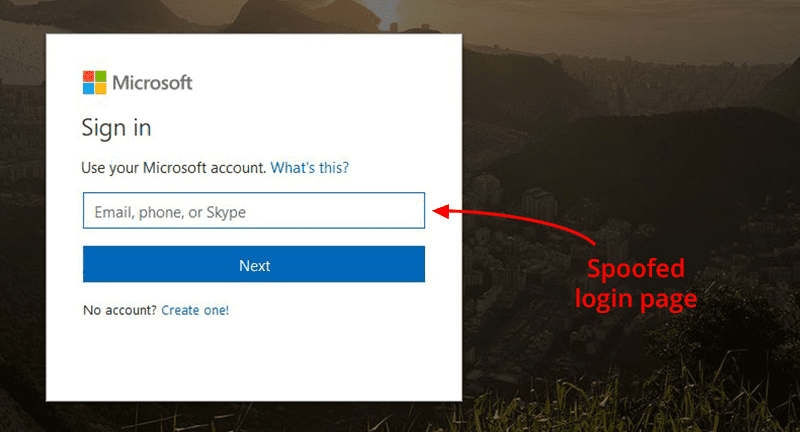
Once clicked, a fake office 365 login page opens where the unsuspecting user then puts their Office 365 login credentials.
Once the user logs in the attacker has stolen their credentials and can start a campaign to defraud the business or to get further within the organisation by spear phishing them from the account. They can also start emailing your customers those same links which makes it even more convincing. To stop detection they will setup rules within your email so that you don’t see any replies coming in from users they are emailing the fake links to, after all this would give the game away.
Attacks are becoming increasingly sophisticated and the key to protecting your data is to take a layered approach to your security. A proven anti-malware service, user education, utilising Multi Factor Authentication within your Office 365 account and enabling DNS filtering solution such as Cisco Umbrella.
Tell users that they should ignore any SharePoint document sharing requests they are not expecting and lookout for tell tale signs in the language used within emails such as “Urgent”, “Action Required” or “Your account will be deleted or suspended”
If the email comes from within your organisation double check with them if anything sounds off with the way the message sounds. If you do not know the person sending you the link do not open it.
One of the easiest ways to secure your account is to use the multi factor authentication that comes with your Office 365 subscription, this will usually stop the attack dead as the attacker will not have access to your second level authentication.
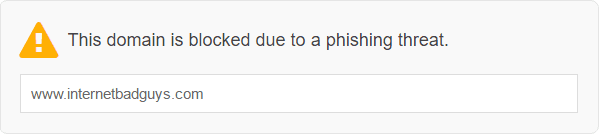
Lastly Cisco Umbrella monitors the internet for malicious sites and blocks them at the DNS level so you cannot get to them from your internet browser. So in the event that a user falls for the attack and clicks on the link, Cisco Umbrella will detect it is a malicious phishing site and block access to it, as shown below, before they get a chance to enter their credentials.
If you need help with securing your users from external threats then please get in touch below.
